Public and private keys are important in PGP to encrypt and decrypt the data. Public key is used to encrypt data and shared with end-users. The Private key is used to decrypt the encrypted data.
Generating Keys
There are many tools available to generate PGP private and public keys. In this article, we will use Git Bash to generate private and public keys.
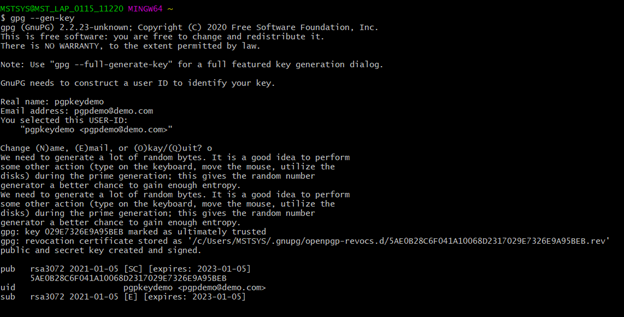
Step 1 : Go to Git Bash > Run > gpg --gen-key
Step 2 : Give “Real name” .
Step 3 : Enter “Email address”.
Step 4 : Enter “Passphrase”. ( Store the passphrase. It will be used in decryption )
Now public and secret key created and signed.
Exporting Generated Public Key
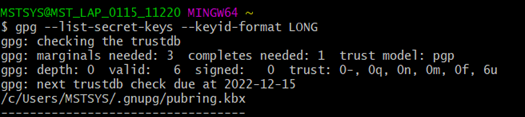
Step 1 : Use this command to list GPG keys for which you have both a public and private key.
gpg –list-secret-keys –keyid-format LONG
Step 2 : Paste the below command to export the generated Public key to desired location.
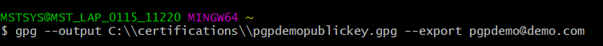
gpg –output C:\\certifications\\pgpdemopublickey.gpg –export pgpdemo@demo.com
Here ,
C:\\certifications -> Directory and Folder name to store the public key file.
pgpdemopublickey.gpg -> Name for the public pgp key file with extension. Extension can be .gpg,.bin
pgpdemo@demo.com -> Email Address that we gave during key generation.
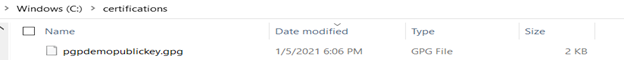
After the above command is run, the public key file will be exported to the folder location specified.
Exporting Generated Private key
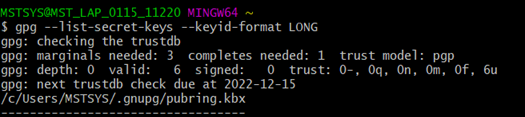
Step 1 : Use this command to list GPG keys for which you have both a public and private key.
gpg –list-secret-keys –keyid-format LONG
Step 2 : Paste the below command to export the generated Private key to desired location.
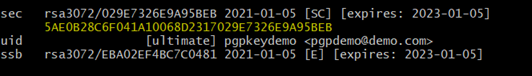
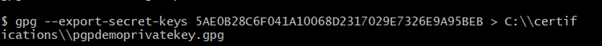
gpg –export-secret-keys 5AE0B28C6F041A10068D2317029E7326E9A95BEB > C:\\certifications\\pgpdemoprivatekey.gpg
Here ,
5AE0B28C6F041A10068D2317029E7326E9A95BEB -> Key
C:\\certifications -> Directory and Folder name to store the Private key file.
pgpdemoprivatekey.gpg -> Name for the private key file with extension. Extension can be .gpg,.bin
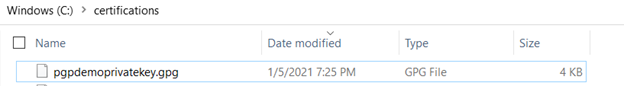
After the above command has run, the private pgp key file will be exported to the folder location specified.
Getting/Identifying Fingerprint for the Generated Keys
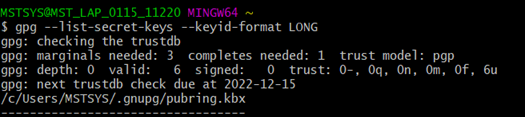
Step 1: Use this command to list GPG keys for which you have both a public and private key.
gpg –list-secret-keys –keyid-format LONG
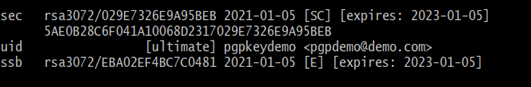
Note: 1) This Command will list all the GPG keys that were generated. Desired GPG keys will be uniquely identified with “Real Name” and “Email Address” that were given during key generation.
2) The Last 16 digit of the row “sec” is the fingerprint.
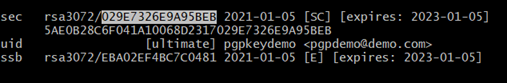
Here,
029E7326E9A95BEB -> Fingerprint ( The Last 16 digit of the row “sec” )
PGP Encryption in Mule 4
1) In Anypoint Studio Go-to -> Mule Palette -> Search in Exchange -> Crypto.
2) Add the Crypto Module to your Mule Palette.
3) From Mule Palette drag and drop Pgp encrypt connector to your flow.
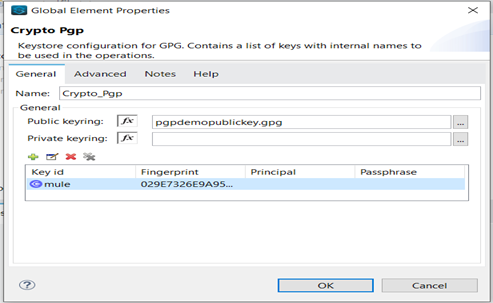
4) In “Module configuration” of “Pgp encrypt” connector, provide the following details:
1) Public Key file.
2) Key id.
3) FingerPrint.
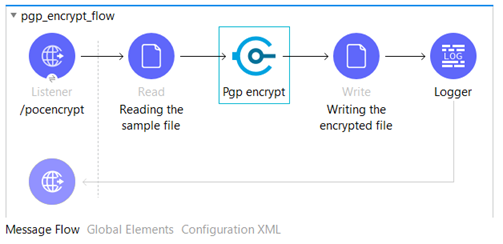
Below is the Sample flow for Reading .TXT file and encrypt its content using PGP Encryption.
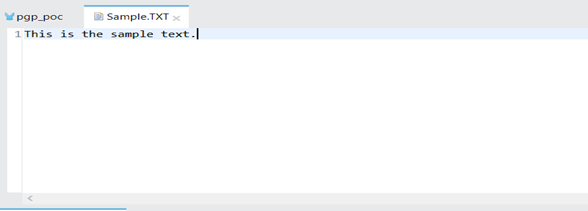
Sample .TXT file
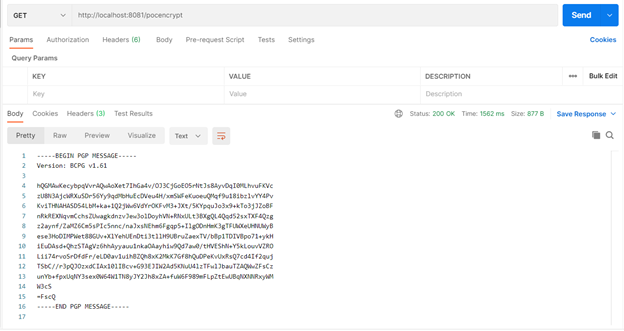
Encrypted content of Sample .TXT file
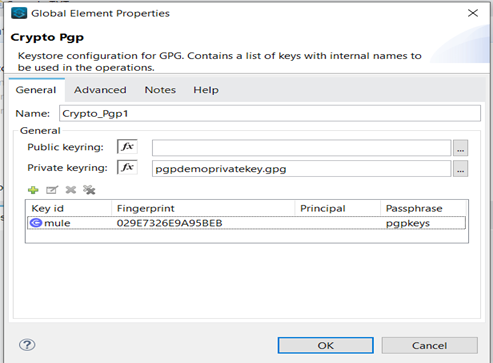
PGP Decryption in Mule 4
1) In Anypoint Studio Go-to -> Mule Palette -> Search in Exchange -> Crypto.
2) Add the Crypto Module to your Mule Palette.
3) From Mule Palette drag and drop Pgp decrypt connector to your flow.
4) In “Module configuration” of “Pgp decrypt” connector, provide the following details.
- Private Key file.
- Passphrase for the private key file.
- Key Id
- Fingerprint .
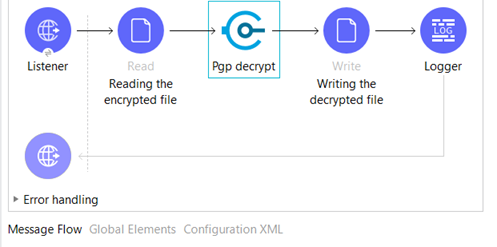
Below is the Sample flow for Reading encrypt file and decrypt its Content using PGP Decryption.
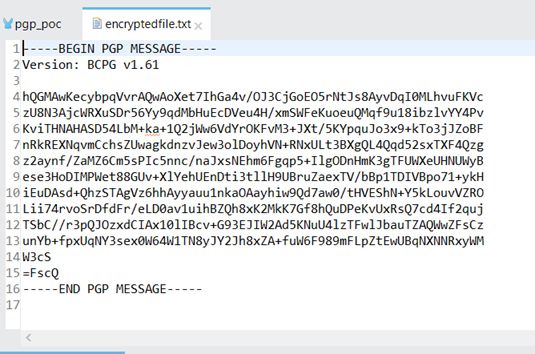
Sample Encrypted File
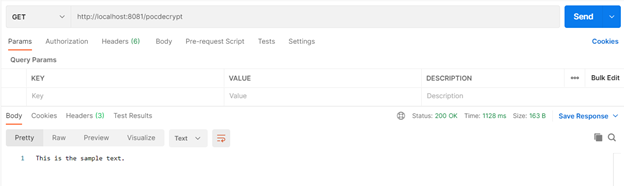
Decrypting Content of Encrypted file