Overview
To protect the application data and maintain the customer trust, Salesforce Introduced Salesforce Shield. Salesforce Shield offers a powerful set of tools for any customer who needs an extra level of control to meet internal or regulatory compliance requirements. Salesforce Shield Available in Enterprise, Performance, and Unlimited Editions. Available in Developer Edition at no charge for organizations created in Summer ‘15 and later.
Balancing data security with business needs:
1. Encrypt sensitive data when it’s stored at rest in the Salesforce cloud.
2. Support customer-controlled encryption key lifecycles.
3. Preserve application and Salesforce1 Platform functionality.
4. No Hardware, No Software.
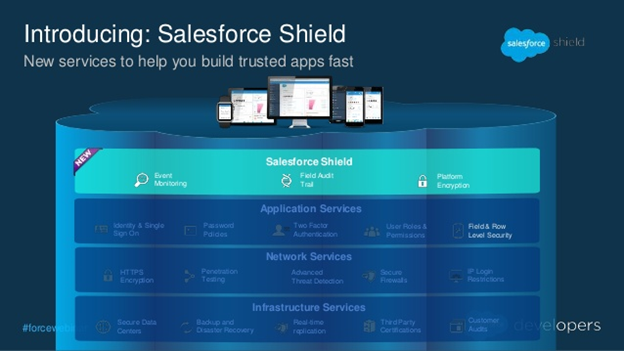
Salesforce Shield Components:
Salesforce Shield is made up of three components:
1. Platform Encryption.
2. Event Monitoring.
3. Field Audit Trial.
Available in: Enterprise, Performance, and Unlimited Editions. Available in Developer Edition at no charge for organizations created in Summer ’15 and later.
Platform Encryption:
Platform Encryption allows you to encrypt fields, files, and attachments stored in the Salesforce1 Platform. In contrast to Classic Encryption, which uses a custom field type in the Salesforce data model, Platform Encryption allows you to encrypt several standard fields and custom field types using metadata while preserving functionality necessary to perform common business tasks in Salesforce. Salesforce administrators can:
Encrypt files and attachments.
1. Encrypt the following standard fields: Account Name, Contact Name, Mailing Address, Phone, Fax, Mobile, Home Phone, Other Phone, and Email.
2. Encrypt the following custom field types: Text, Text Area, Text Area (Long), Phone, Email, and URL.
3. Manage the lifecycle of data encryption keys.
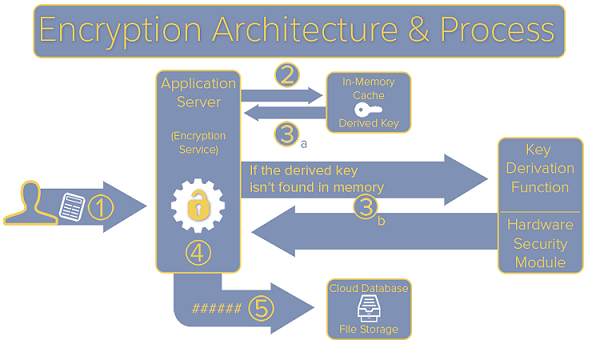
Seamlessly protect data at rest
1. Encrypt standard and custom fields, files and attachments.
2. The data is protected at rest mainly because to protect against unauthorized database access.
Enabling Platform Encryption:
Go to Setup > Security Controls > Platform Encryption and then click Create Tenant Secret.
Platform Encryption uses the Java Cryptography Extension (JCE), to encrypt and decrypt data. Specifically, Platform Encryption uses the Advanced Encryption Standard (AES-256)
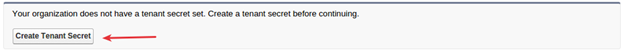
A key will be generated initially under Key Management and the data that users create after generating key will be encrypted by using this New Tenant Secret Key.
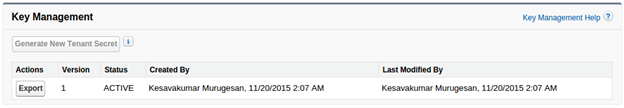
Keys:
Tenant Secret: Generated and rotated by customers. A New Tenant Secret can only be generated once every 24 hours in a production organization and every 4 hours in sandbox environment. The option is disabled, if the Tenant Secret is generated in last 24 hours in production and 4 hours in sandbox environment.
Master Secret: Generated and rotated by Salesforce. Master secrets used in the key derivation function are rotated with each major Salesforce release.
Key Management:
Exporting Keys:
You can export your key to a backup location for safekeeping. Key must be exported before destroying it. If you destroy a key, then any data encrypted with that key can no longer be accessed. Data can be accessed by importing the key.
Destroying Keys:
Once the key is destroyed, the data encrypted with that key can no longer be accessed. If you export the key before you delete it, you can import the key back into your organization.
Importing Keys:
Encrypted data can be accessed by importing the key back into your salesforce organization.
Steps to create Custom Encrypted Field:
Go to any custom Object detail page and create new custom field.
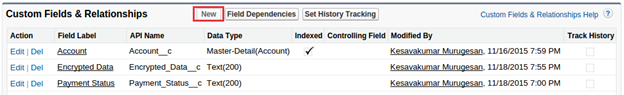
Enable Encrypt the contents of this field checkbox while creating the custom field

Note: Once the encrypted field has been created, then it’s not possible to change the Field Type again.
Platform Encryption supports only the following fields:
| Text | Text Area |
| Text Area(Long) | Phone |
| URL |
Steps to create Standard Encryption Fields:
Go to Setup > Security Controls > Platform Encryption and click Encrypt standard Fields
Following Objects support Platform Encryption:
* Account – Account Name.
* Contact – Name, Mailing Address, Phone, Fax, Mobile, Home Phone, Other Phone and Email.
* Case – Subject, Description.
* Case Comment – Body.
Permissions:
View Encrypted Data: For viewing the encrypted data.
Manage Encryption Keys: For managing keys.
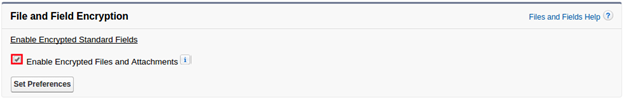
Steps to be followed to encrypt files and attachment:
Select Enable Encrypted Files and Attachments under Platform Encryption settings and click Set Preferences. Encrypted files will be visible to Organization users. They are encrypted at database only.
Limitations in Platform Encryption Fields:
* You can’t use currently or previously encrypted custom fields in custom formula fields or criteria-based sharing rules.
* You can’t use Schema Builder to create an encrypted custom field.
* Fields that have the Unique or External ID attributes or include these attributes on previously encrypted custom fields.
* You can’t encrypt the fields on external data objects.
* If encryption is enabled for standard fields, we cannot enable Community/Portal.
Event Monitoring:
Event monitoring lets you to easily see what data users are accessing, from what IP address, and the actions done to that data. For Example API calls, user logins, users who are running reports, exporting reports, downloading files, and etc.
Use the SOAP API and REST API resources to retrieve event log files that contain information useful for assessing organizational usage trends and user behavior.
You can track up to 28 different event types. Log data is read only. You can’t insert, update, or delete log data.
As per Salesforce documentation, you can access those data via API and pull the data into any visualization tools. For example Salesforce Analytics.
Event Monitoring Supports following Events:
| Apex CalloutApex ExecutionApex SOAPApex TriggerAPIAsync ReportBulk APIChange Set OperationContent Distribution | Content Document LinkContent TransferDashboardDocument Attachment DownloadsLogoutLoginLogin AsMultiblock Report | Package InstallQueued ExecutionReportReport ExportREST APISalesforce1 Adoption (UI Tracking)SandboxSites |
Field Audit Trail
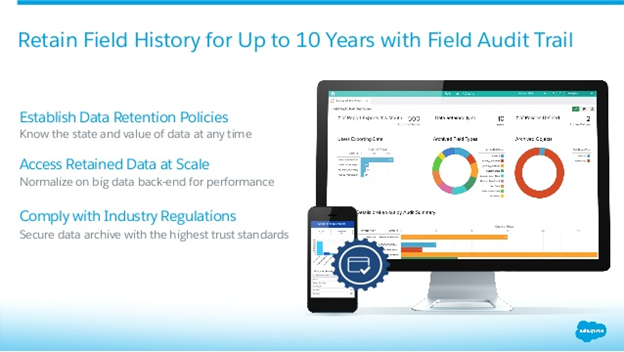
It is used to track information about who, when and what data has changed. Current data retention period is 18 months and we can track up to 20 fields only, but by upgrading to Field Audit Trail with History tracking, we can track up to 60 fields and can retain data for 10 years.
What features and apps don’t support after encryption?
These apps don’t support data that’s encrypted at rest. Check this page for changes to the list of unsupported apps.
| Chatter DesktopConnect OfflineData.comExact TargetExchange SyncFlowsHeroku ConnectLightning ComponentsLightning ConnectPardot | Process BuilderSalesforce App for OutlookSalesforce Classic MobileSalesforce for OutlookSalesforce to SalesforceSite.comVisual WorkflowsWaveWork.com |
Conclusion:
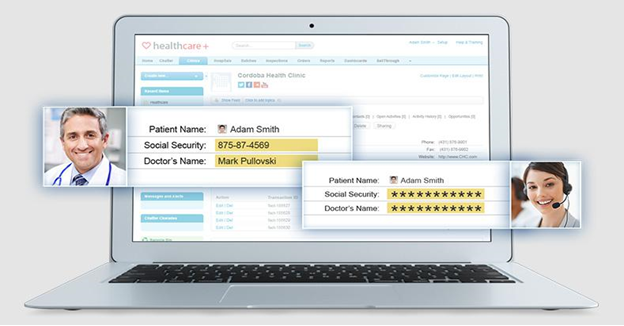
Salesforce shield lets you to protect sensitive data in your organization. For example, using Platform Encryption you can protect the sensitive data, like social security number, credit card number, customer information, and etc. Protected fields are only visible to the users who have the “View Encrypted Data” permission. Encrypted data can only be accessed with appropriate Tenant Secret.
Reference:




