This article will discuss various types of ways we can do secure configuration in the Mule projects. we have taken a few areas as listed below.
- Securing environment properties.
- Securing property files.
- Brief information about securing cloud hub
Securing the environment properties.
In mule 4, the environment properties help work with different levels of deployment & allow easy change of the frequently updated values related to the project without modifying any code. This can be encrypted and placed securely while deploying to cloud hub environment.
For this, we need to use a file called mule-artifact.json. In this file, we need to mention the values for a key named secureProperties, for example, like below:
“secureProperties”: [“anypoint.platform.client_id”,”anypoint.platform.client_secret”]
Securing property files
MuleSoft provides a better way to secure the property files used in mule projects. It provides a wide range of encryption algorithms to work with. Below is the list of few algorithms that can be used in MuleSoft:
- AES (default)
- Blowfish
- Camellia*
- CAST5*
- CAST6*
- DES
- DESede
- RC2
- RCA
- Noekeon*
- Rijndael*
- SEED*
- Serpent*
The algorithms marked with a star(*) need an additional Java cryptography extension provider to configure with the mule projects.
In the above, we saw what algorithms we can use. Next, we are going to see the tools & components we need to understand to implement this encryption.
First, we need a jar tool that helps with encrypting/decrypting our required values. We can get it from the Secure property tool link. Once we have downloaded it, we need to decide whether we are going to encrypt the whole property file or only some of the values in the file.
Whatever the way we choose, the below are the general syntax for doing that:
java -cp secure-properties-tool.jar com.mulesoft.tools.SecurePropertiesTool method operation algorithm mode key value
method: Decides that we are doing the encryption for file-level or string level
operation: Indicates encrypt or decrypt operation.
algorithm: As we discussed earlier, this denotes which algorithm we are using for securing the data
mode: It a value used by the mule runtime with the blocks & cipher. Possible values can be CBC (default), CFB, ECB, and OFB
key: The key is the cipher word we use for our encryption or decryption.
value: It can be a file or simple string value that needs to be encrypted or decrypted.
java -cp secure-properties-tool.jar com.mulesoft.tools.SecurePropertiesTool file encrypt AES CBC $amplekey0087654 errormsgs.yaml errormsgs-enc.yaml
Mule supports two types of files .properties & .yaml files.
Additionally, Mule provides
- the cipher key & file that can be managed with runtime environment values which help even more security based on different environments.
- Multiple secure property files can be added based on different needs.
Implementation:
in <global>-cong.xml file
<secure-properties:config key=”${environment.property}” file=”file2.yaml” name=”seureConfig”>
<secure-properties:encrypt algorithm=”DES” mode=”CBC”/>
</secure-properties:config>
We can use the same tags to use more than one property file too.
To access the secure values inside the mule code, we need to use alike ${secure::property-key}.
Example:
${secure::db-user}
The property file can contain both encrypted values & as well as non-encrypted values.
Brief information about securing cloud hub
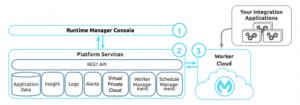
Cloud hub is an integration Platform as a service provided by MuleSoft. They provide security in different ways. Users, Private subnets, and as we have seen above by securing properties
Below is the architecture diagram of the Cloud hub
In the above, we discussed the security configurations in a simple way, how it can be achieved, and how to make the Mule projects secured as per standards.
References
For additional inputs please check on the below



